Exploring the World of Containerization: A Closer Look at IPC and UTC
Exploring How Linux Manages Process Communication and System Names
Welcome to the second installment of our blog series, "Exploring the World of Containerization: A Journey Through Linux Namespaces." Continuing our exploration of the intricate world of containerization, we delve deeper into the foundational elements that make this technology so vital in today's software landscape.
In this part, we shift our focus to two crucial types of Linux namespaces: IPC (Interprocess Communication) and UTS (UNIX Time-Sharing System). Building on the analogy we used previously, we'll unfold these complex concepts in a way that's engaging and easy to grasp, shedding light on the sophisticated mechanisms behind process communication and system identity in container environments.
If you missed the first part of our series, where we laid the groundwork by discussing filesystem isolation, I encourage you to start there for a comprehensive understanding. You can find it here: Exploring the World of Containerization - Part 1.
Join us as we continue our journey through the fascinating landscape of Linux namespaces, uncovering the secrets that power containerization in the modern tech world.
Do you remember our journey through "Harbor Haven" from the first part of our series? We embarked on an adventure of isolating each of our users' processes (think of them as individual rooms) and their respective amenities (akin to mounts). This isolation ensured that each user's activities were confined to their own private space, free from interference from others.
But now, we've encountered a new challenge. Our guests don't want to be identified by random numbers or generic names. Instead, they seek to have their own distinct identities, names that resonate with their individuality and purpose. This is where we introduce the concept of UTS (UNIX Time-Sharing System) namespaces.
UTS: Identity in Isolation – More Than Just Time-Sharing
Welcome to the realm of UTS namespaces in Linux! This powerful feature allows each guest (or container, in technical terms) to have its own hostname. Imagine walking down the corridors of Harbor Haven, where every door (container) has a unique nameplate, not just a room number. This individual naming is not just about preference; it’s crucial for our guests to operate independently, ensuring that their communications and interactions are correctly attributed and managed.
In our virtual Harbor Haven, UTS namespaces are like giving each room the ability to display its own, unique name, distinct from every other room. It’s not just about uniqueness; it's about giving identity and a sense of belonging to each isolated environment.
So, as we continue our exploration through the intricate world of containerization and Linux namespaces, let's dive into the fascinating concept of UTS namespaces. Here, every guest gets to say, "This is my space, and this is my name!"
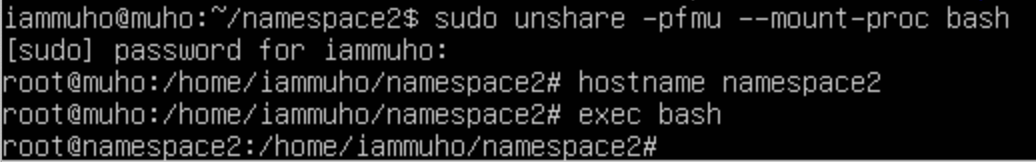
To create a UTS namespace in addition to the other namespaces we've set up earlier, simply include the -u (UTS) flag in the unshare command. This allows for an isolated environment where the hostname can be distinct from the parent system.
sudo unshare -p -f -m -u --mount-proc /bin/bashOnce you're in this newly created namespace, you can assign a unique hostname to it. For example, to set the hostname for this namespace to namespace2, use the hostname command:
hostname namespace2After setting the hostname, it's a good practice to refresh the shell to ensure the new settings take effect. You can do this by executing:
exec bashAs you can see, now the UTS are isolated. Let’s confirm this by checking the lsns with other namespace.As we have seen at the first at the first tutorial, I’ll just put the output screenshots.
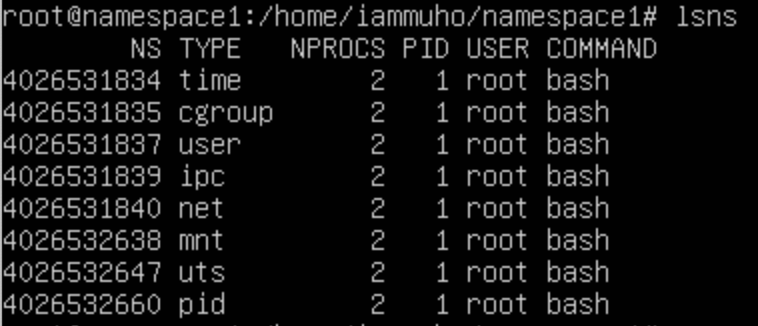
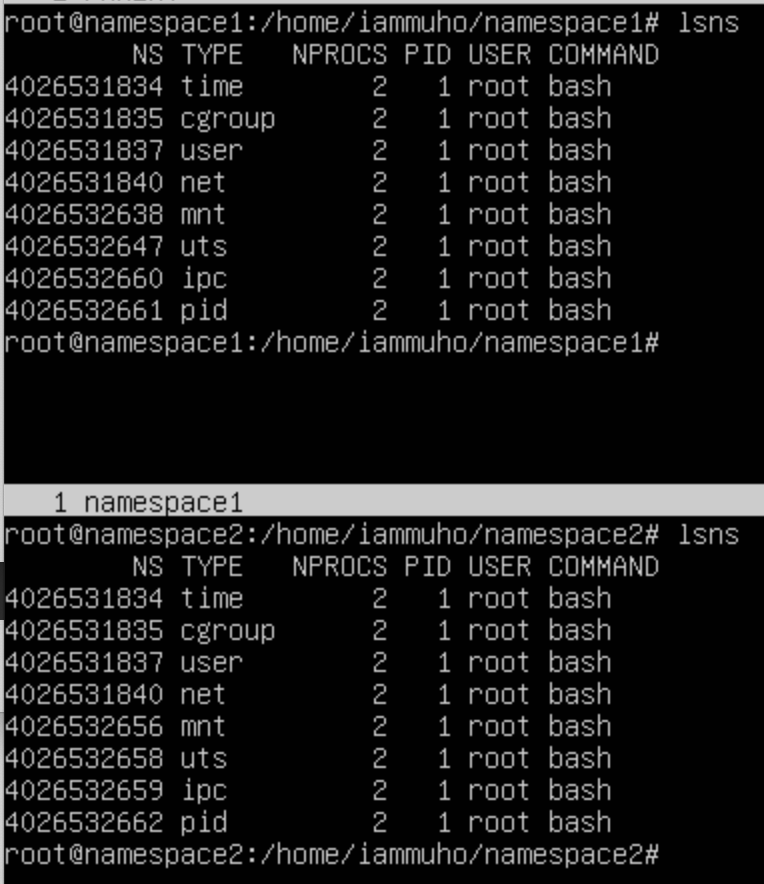
Namespace1:
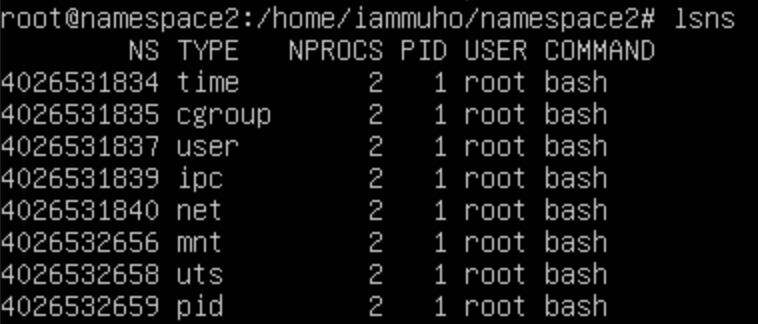
Namespace2:
Observe the distinct namespace (NS) IDs for PID, MNT, and UTS. These indicate that these specific namespaces have been isolated and are separate from the parent namespace. The remaining namespaces continue to be shared with the parent, maintaining their original settings and associations.
Great! We've successfully fulfilled another request of our guests at Harbor Haven. Now, each guest can name their own room (or in technical terms, their namespace) whatever they wish. This added layer of customization in UTS namespaces enhances the sense of individuality and control within their isolated spaces.
But is our journey through the world of containerization and namespaces over? Not quite! Our guests, always eager for more refined experiences, have yet another request. What could it be this time ?
IPC: Mastering Communication in Isolated Spaces
The requests never cease at Harbor Haven. Our hotel management has been inundated with a new set of requests from guests seeking more privacy and efficiency in their communications. Guests have expressed a need for separate telephone lines within their rooms for internal conversations. They've found that relying on the standard hotel lines often leads to busy signals and congestion, not to mention concerns about privacy when discussing confidential matters.
Envision a scenario where each room at Harbor Haven is equipped with a dedicated internal telephone system. This system allows guests to communicate freely within their own space, ensuring that their conversations are both secure and uninterrupted by external calls. This setup mirrors the concept of IPC (Interprocess Communication) namespaces in Linux, where processes within the same isolated environment can communicate privately, free from the noise and security concerns of the wider system.
To establish an IPC (Interprocess Communication) namespace alongside the other namespaces we have already set up, we simply add the -i flag to the unshare command. This step creates an environment where various IPC mechanisms, like message queues, are isolated from the parent system.
Execute the following command to create a combined namespace with PID, mount, UTS, and now IPC isolation:
sudo unshare -p -f -m -u -i --mount-proc /bin/bash Once inside this newly created namespace, we can illustrate IPC isolation through the creation of message queues. These queues will be unique to each namespace, demonstrating the isolated nature of IPC.
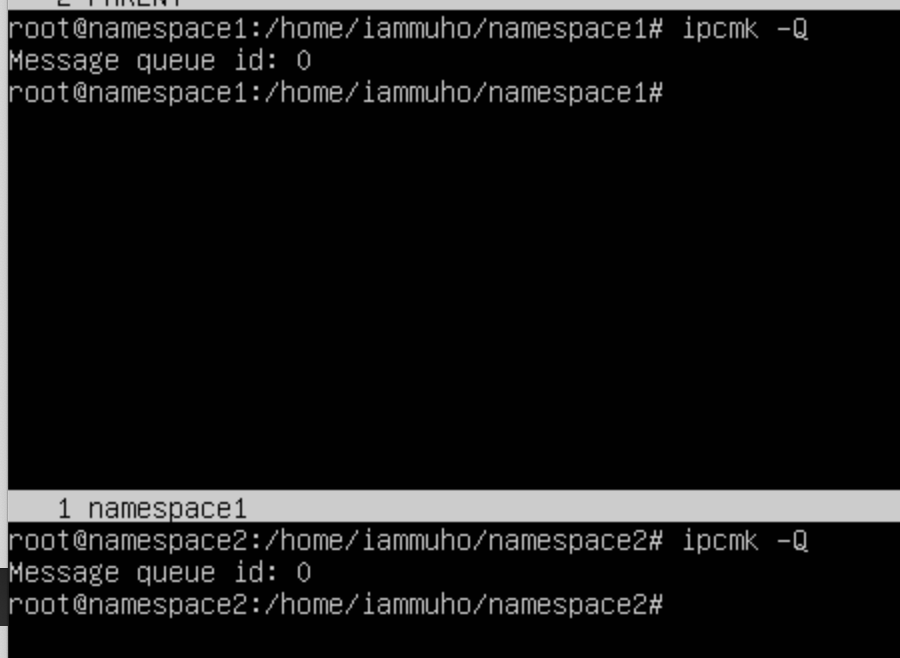
To do this, we'll create a new message queue in both namespaces using the ipcmk command:
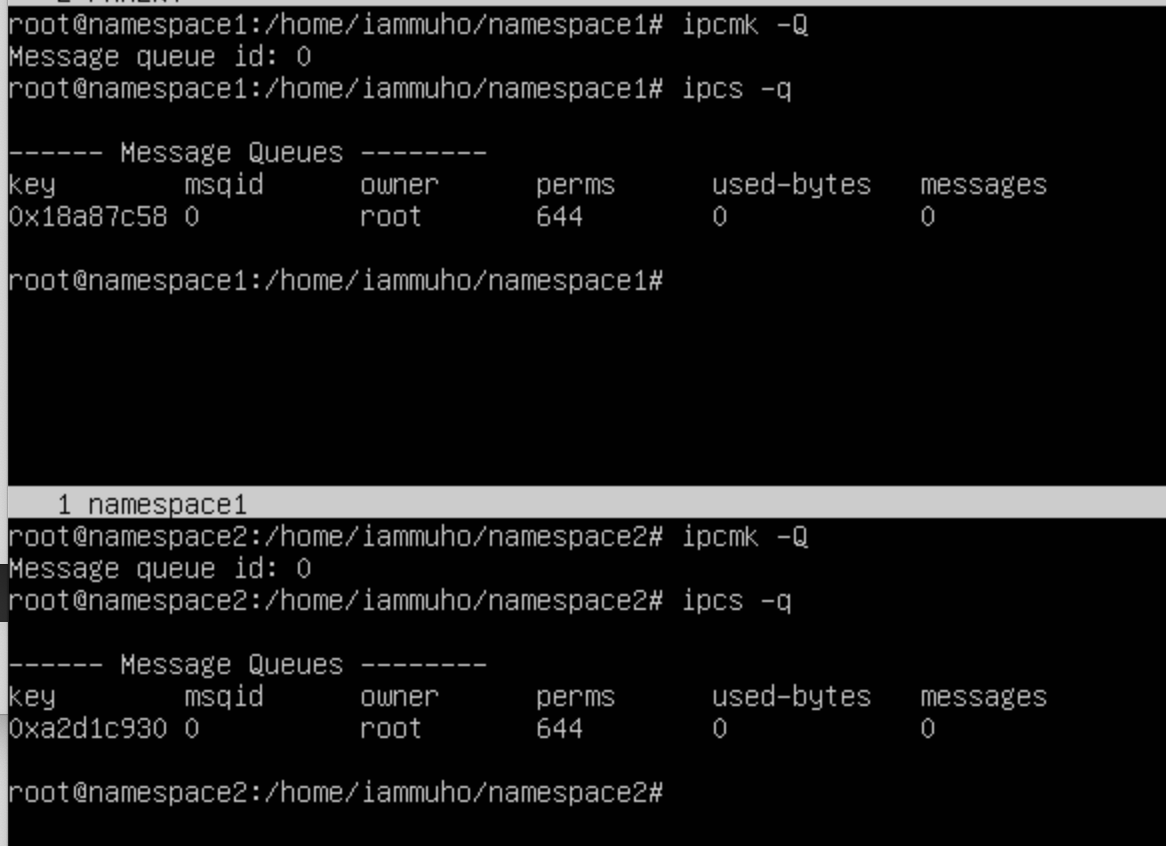
ipcmk -QTo view the message queues within our newly created IPC namespace, the ipcs -q command comes into play. This command is specifically designed to display information about the active message queues in the current namespace. Here's a brief on how it works:
ipcs -qBy performing these steps, we effectively set up distinct IPC namespaces where each namespace can manage its own interprocess communication mechanisms, free from interference or visibility from outside its boundaries.
Last time, we can use the lsns utility to see if the IPC namespace has been isolated too;
Example: Using IPC in Docker Containers
Scenario: Let's say you're running a Docker container that hosts a web application. This application includes a main web server process and a secondary logging process. These processes need to communicate with each other – the web server sends log messages to the logging process.
IPC Usage:
Isolated Communication: When you run a Docker container, it can be configured to have its own IPC namespace. This means the communication between the web server and the logging process is isolated within that container. Even if there are other containers running on the same host, their processes cannot see or interfere with the IPC mechanisms of your container.
Message Queues: The application might use message queues for inter-process communication. In the isolated IPC namespace of the container, a message queue is created for the web server process to send log messages, which the logging process reads and processes.
Security and Congestion: By having a dedicated IPC namespace, Docker ensures that the communication between processes in one container is secure and free from congestion from other containers. This is crucial in a multi-container environment where each container might host different applications with their own inter-process communication needs.
Example Docker Command:
docker run --ipc=private my-web-appThis command runs a Docker container with the web application and ensures it has a private IPC namespace. Any IPC resources created by the application will be confined to this container.
In this example, Docker utilizes IPC namespaces to provide a secure and isolated environment for the web server and logging processes to communicate, enhancing both the security and reliability of the application. This approach is fundamental in containerized environments, where isolation and resource management are key.
As we conclude this second part of our journey through "Harbor Haven" and the world of Linux namespaces, we've uncovered the vital roles of IPC and UTS namespaces. These namespaces not only enhance the isolation of processes within containers but also provide unique identities and secure communication channels.
In Harbor Haven, our guests now enjoy the luxury of private, internal telephone lines (IPC namespaces) and the freedom to name their rooms (UTS namespaces). This enhanced level of customization and isolation mirrors the sophisticated environment provided by containerization technologies in the tech world.
However, our exploration doesn't end here. The world of Linux namespaces is vast and multi-faceted. There are still more layers to uncover, more requests from our guests to fulfill. What new features will they ask for next? How will we continue to evolve Harbor Haven to meet these demands? These questions will lead us into the next exciting part of our series.
Stay tuned as we delve deeper into the remaining namespaces and their practical applications in Linux and containerization. The journey through the intricate world of Linux namespaces is far from over – there's much more to learn, understand, and explore.